Which Two Ipsec Protocols Are Used to Provide Data Integrity
AES is an encryption protocol and provides data confidentiality. To protect network data by setting up circuits using IPsec tunneling in which all data is being sent between the two endpoints is encrypted as with a Virtual Private NetworkVPN connection.
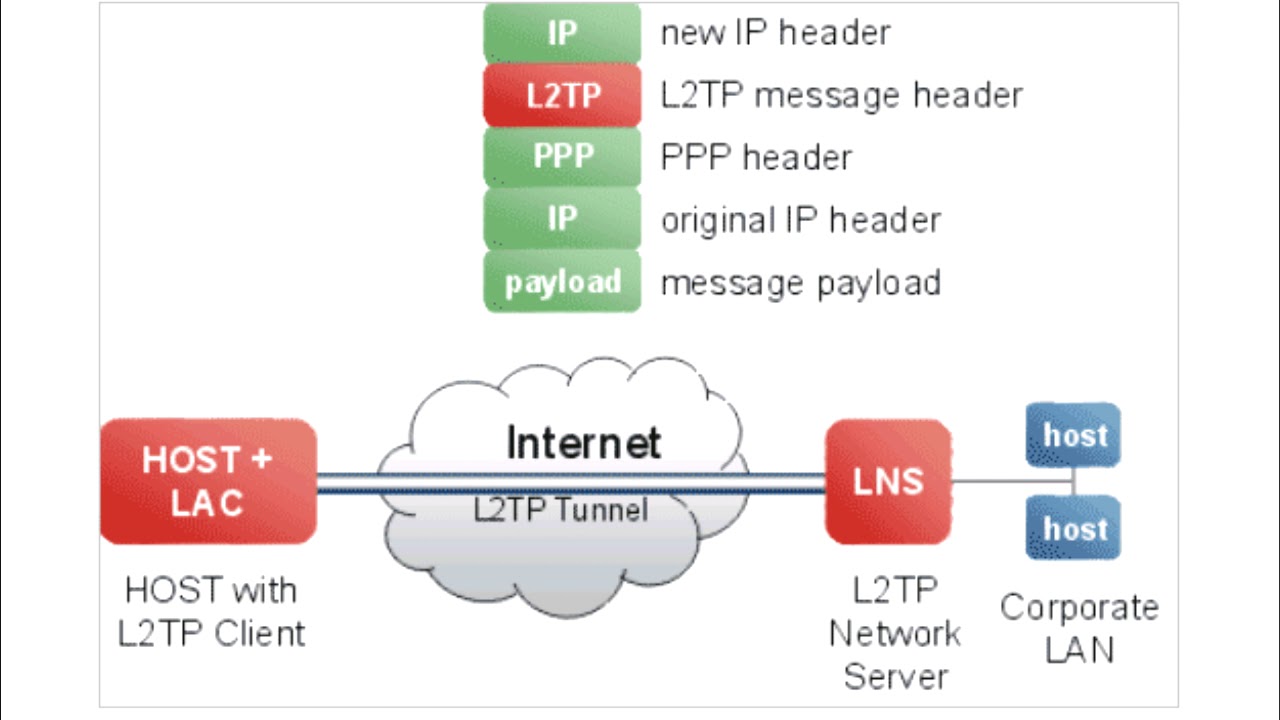
Which Of The Following Protocols Are Utilized By Ipsec Vpn
AES is an encryption protocol and provides data confidentiality.
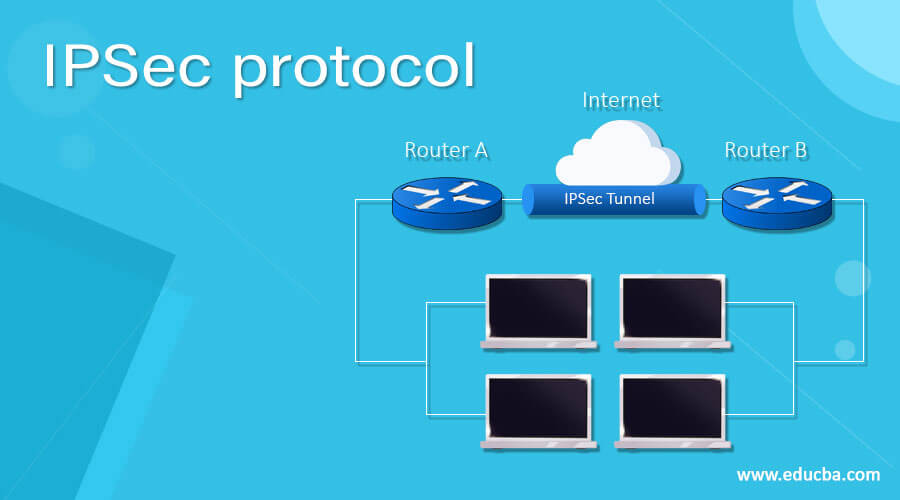
. Encapsulating Security Payload ESP It provides data integrity encryption authentication and anti replay. It is simply inserted between the IP header and any subsequent packet contents. IPSec authentication header protocol is a header in an IP packet that contains a cryptographic checksum for the concept of packets.
IP Security ProtocolEncapsulating Security Payload ESP Encapsulating Security Payload ESP is a security protocol used to provide confidentiality encryption data origin authentication integrity optional antireplay service and limited traffic flow confidentiality by defeating traffic flow analysis. Which two IPsec protocols are used to provide data integrity. What is the function of the Diffie-Hellman algorithm within the IPsec.
The integrity component of the CIA triad ensures that data is not modified in transit by unauthorized parties. AES MD5 The IPsec framework uses various protocols and algorithms to provide data confidentiality data integrity authentication and secure key exchange. The IPsec framework uses various protocols and algorithms to provide data confidentiality data integrity authentication and secure key exchange.
Which two IPsec protocols are used to provide data integrity. This authentication header is inserted in between the IP header and any subsequent packet contents. The IPsec framework uses various protocols and algorithms to provide data confidentiality data integrity authentication and secure key exchange.
The IPsec framework uses various protocols and algorithms to provide data confidentiality data integrity authentication and secure key exchange. VPN uses two IPSec protocols to protect data as it flows through the VPN. Authentication Header AH and Encapsulating Security Payload ESP.
AH is protocol number 51 and provides data authentication and integrity for IP packets that are exchanged between the peers. The IPSec authentication header is a header in the IP packet which contains a cryptographic checksum for the contents of the packet. The Correct Answer for this Question is.
Components of IP Security It has the following components. The two primary protocols used with IPsec are AH and ESP. AES is an encryption protocol and provides data confidentiality.
Encapsulating Security Payload ESP Security protocol that provides data privacy services optional data authentication and antireplay services. Originally Internet Protocol Security defined only two protocols for securing the IP packets which were Authentication Header AH and Encapsulating Security Payload ESP. AH provides data integrity and non-replay services and the latter protocol ie.
Two popular algorithms that are used to ensure that data is not intercepted and modified data integrity are MD5 and SHA. Two popular algorithms that are used to ensure that data is not intercepted and modified data integrity are MD5 and SHA. DH Diffie-Hellman is an algorithm used for key exchange.
AES is an encryption protocol and provides data confidentiality. Correct Answer for the Question Which two IPsec protocols are used to provide data integrity. DH Diffie-Hellman is an algorithm used for key exchange.
The two primary protocols used with IPsec are AH and ESP. Authentication Header AH A security protocol that provides data authentication and optional antireplay services. Two popular algorithms used to ensure that data is not intercepted and modified data integrity are MD5 and SHA.
The former protocol ie. ESP which is protocol number 50 performs packet encryption. AH and ESP are integral parts of the IPSec protocol suite and can be used to ensure the integrity of a packet.
Provide the integrity component of the confidentiality integrity and availability CIA triad. The other part of IPSec enablement is the Internet Key Exchange IKE protocol or key management. If the data generates the same checksum value on each end of the connection the data was not modified in transit.
ESP which is protocol number 50 performs packet encryption. The two primary protocols used with IPsec are AH and ESP. IP Security IPSec Protocol.
AH is protocol number 51 and provides data authentication and integrity for IP packets that are exchanged between the peers. Two popular algorithms used to ensure that data is not intercepted and modified data integrity are MD5 and SHA. AES is an encryption protocol and provides data confidentiality.
The authentication header protocol provides integrity authentication and anti-replay service. AH and ESP are integral parts of the IPSec protocol suite and can be used to ensure the integrity of a packet. Two popular algorithms used to ensure that data is not intercepted and modified data integrity are MD5 and SHA.
Data integrity is provided by using checksums on each end of the connection. The Correct Answer for this Question is. DH Diffie-Hellman is an algorithm used for key exchange.
The IPsec framework uses various protocols and algorithms to provide data confidentiality data integrity authentication and secure key exchange. The authentication header protocol provides features like authentication integrity and anti-replay. AH is embedded in the data to be protected a full IP datagram.
ESP encrypts and authenticates data. DH is a public key exchange method that allows two IPsec peers to establish a shared secret key over an insecure channel. The IPsec framework uses various protocols and algorithms to provide data confidentiality data integrity authentication and secure key exchange.
RSA is an algorithm used for authentication. Correct Answer for the Question Which two IPsec protocols are used to provide data integrity. AH is protocol number 51 and provides data authentication and integrity for IP packets that are exchanged between the peers.
ESP which is protocol number 50 performs packet encryption. DH is a public key exchange method that allows two IPsec peers to establish a shared secret key over an insecure channel.

Ipsec Is A Suite Of Protocols Defined By The Internet Engineering Task Force Ietf To Provide Security Services At The Network Layer Standard Protocol Ppt Download
Network Security And Protocols

Ipsec Framework S600 E V200r019c00 Configuration Guide Vpn Huawei

Chapter 13 Ipsec Ipsec Ip Security A Collection Of Protocols Used To Create Vpns A Network Layer Security Protocol Providing Cryptographic Security Ppt Download

Ipsec Detailed Description And Vpn Ppt Download

A Primer On Ipsec Vpn Cloud Blog Vmware

Which Of The Following Protocols Are Utilized By Ipsec Vpn

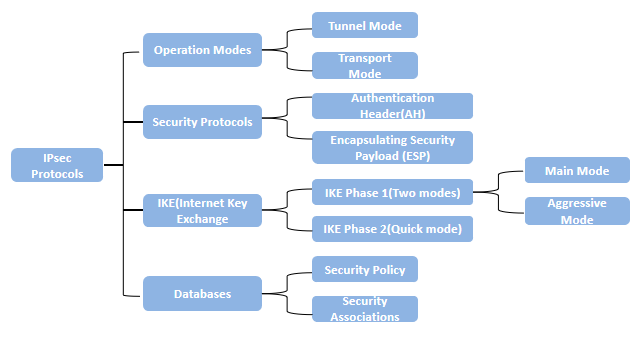
Ipsec Protocol Different Protocol Of Ipsec In Detail

Computer Networking Model And Set Of Communications Protocols Used On The Internet It Is Networking Basics Networking Infographic Computer Science Programming

What Is Ip Security Ipsec Tacacs And Aaa Security Protocols







Comments
Post a Comment